Timing Based Encryption: Test Case 3
Test Case 3: Eve on the same network as Bob/Alice
This was the third test done on the timing based protocol, and was conducted using three machines - representing Alice, Bob and Eve respectively running three python scripts: AliceTS.py, BobTS.py, EveTS.py. These scripts recorded the round trip times - and these round trip times were subsequently fed into a Matlab file for post analysis. The scripts and Matlab file are available here and here respectively. The set up for this test was running the Alice script on Michael's home machine, and the Eve/Bob scripts were run on my machines. This created the scenario where Eve/Bob are on the same network, while Alice was on a different network.
In this situation, when Eve and Bob are on the same network, this may potentially mean that the difference between Bob and Eve's round trip times, and consequently bit streams, is so minuscule that the bit parity checks are just as effective for Eve as they are for Alice and Bob.
Test Run 1
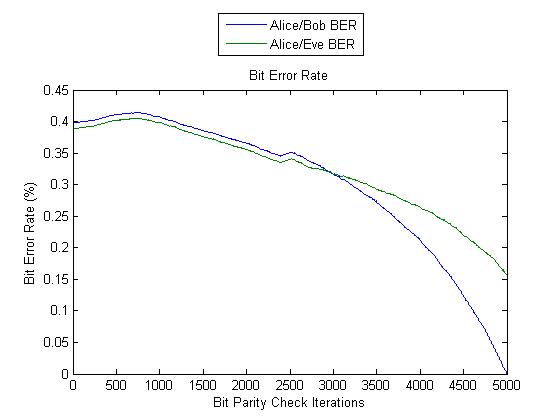
The first test run was done using 10000 round trip times. It showed favourable behaviour, as even though the Alice/Bob bit error rate was originally higher than the Eve/Alice bit error rate it dropped much quicker. At the end of the reconciliation, the Alice/Bob bit error rate had reached zero and the Eve bit error rate was still at 15%. Even though this test was potentially meant to be the one which gave the protocol the most trouble, it actually showed better results than either the LAN/Internet testing so far.
Test Run 2
As the first test showed favourable behaviour, this test also used 10000 round trip times. However, the second test run began to show us the problems which we had anticipated. It appeared that the round trip times which Bob/Eve had generated were so similar that even though the protocol still showed it was more effective for Bob/Alice (as we can see it drops ever so slightly faster) it was very effective for Eve as well.
Test Run 3
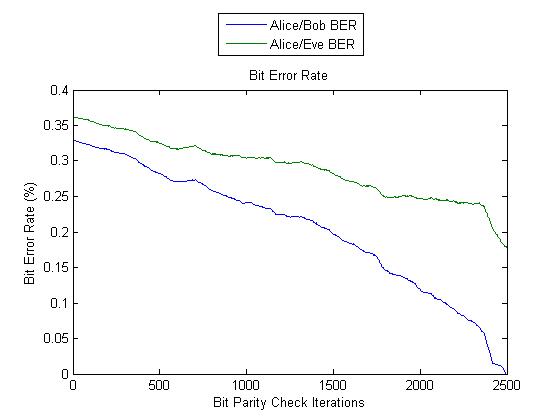
As the first two tests showed us that regardless of the amount of round trip times, we can get good and bad results - this test was run with slightly less round trip times, 5000. Test 3 again showed us favourable results, as from beginning to end the Bob/Alice bit error rate was lower and also dropped at a much lower rate. Eve's bit error rate finished at 17.5%, one of our best results yet.
Test Run 4
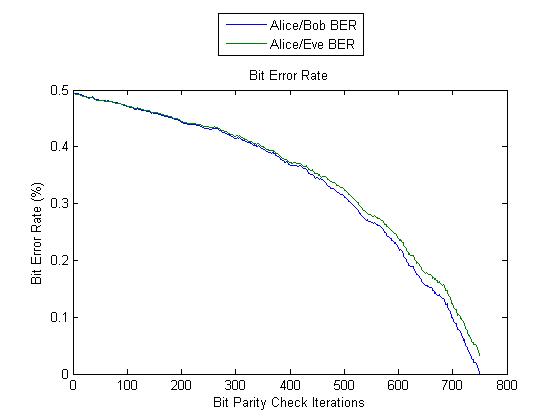
As we seemed to get better results when we lowered the amount of round trip times, they were again lowered for test 4, this time to 1500. However, this test run showed similar results to Test 2, however not as severe. In this case, even though the Alice/Eve bit error rate is very close to the Alice/Bob bit error rate, it finished at 5% instead of 1%.
Summary of Results
In addition to the test results shown on this page, there were several others run which confirmed what was shown on this page. The amount of successful/unsuccessful test runs was split approximately 70/30. For this test case, there appeared to be an element of luck involved, as despite repeating the same tests under the same circumstances we got different results. As expected, this scenario where Eve is on the same LAN as either the sender/recipient is the least successful case in which the protocol can run. However, even though it is the least successful, it should be noted that it still is successful. Additionally, when talking about communications, given the low probability that Eve will be on the same network as either the sender/recipient this randomness is acceptable.
See also
- Timing-based key agreement
- Timing Based Encryption: Test Case 1
- Timing Based Encryption: Test Case 2
- Timing Based Encryption: Test Case 3
- Timing Based Encryption: Test Case 4
- Timing Based Encryption: Test Case 5
- Geometric Algebra
- CLUViz Geometric Algebra Animation Software
- Secure communications without key exchange (main page)
- Secure communications without key exchange? 2013 weekly progress
- Proposal Seminar 2013: Secure communications without key exchange?
- Final Seminar 2013: Secure communications without key exchange?
- Semester A Progress Report 2013 - Secure communications without key exchange?
- Semester B Final Report 2013 - Secure communications without key exchange? 2013
- YouTube Videos