Timing Based Encryption Simulations
Timing Based Key Encryption Simulations
Before any significant work on the timing based key encryption protocol was done, a series of simulations were done in Matlab to test the viability of the approach. The results are shown below, and the code is available here
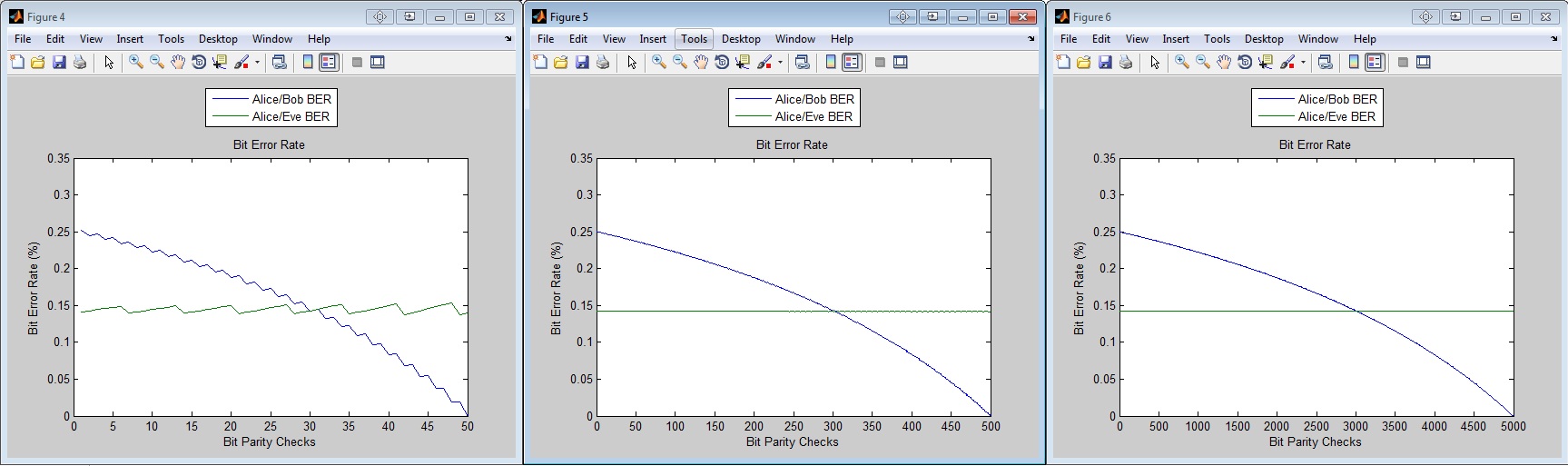
Test Case 1
Test case 1 was performed by performing bit parity checks on three strings, which are randomly generated, of size N = 100, N = 1000, N = 10000
The results show that the Alice/Bob bit error rate drops as we perform bit parity checks, as we would expect, however due to the fact that the eavesdroppers stream is completely randomly generated, the bit parity checks are completely useless for the eavesdropper and thus their bit error rate does not drop at all.
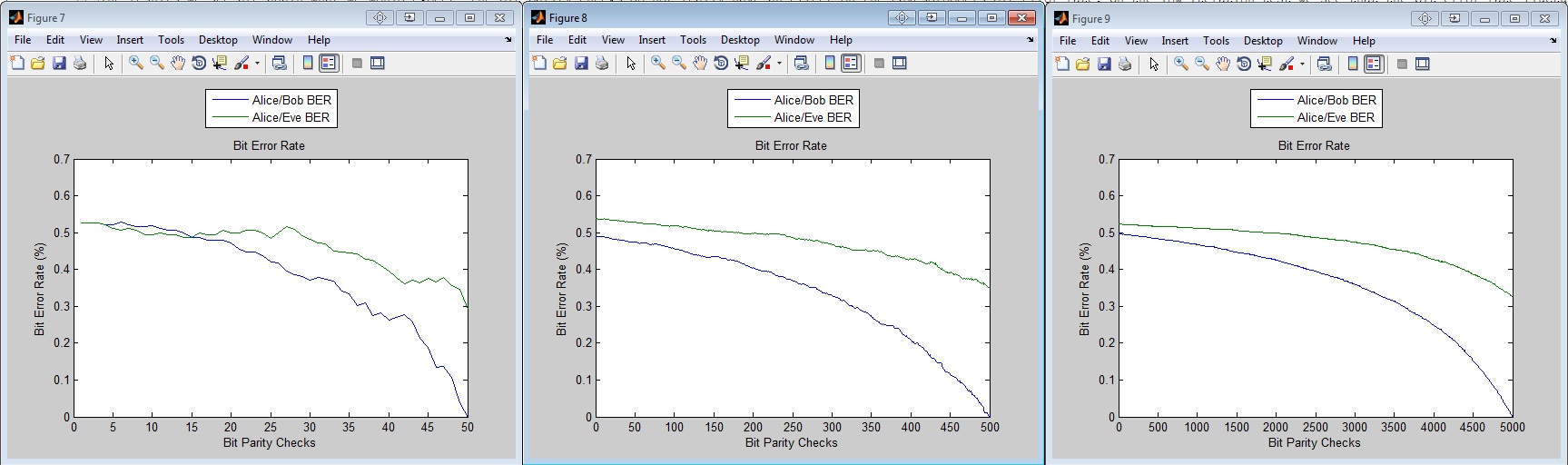
Test Case 2
Test case 2 was a more realistic scenario which we would expect, where the Eve, Bob bit streams are slight mutations of the original bit stream, instead of being completely random. This is done by selecting a bit error rate for Bob and Eve (1/7, and 1/4 are used respectively) and then every 4th of 7th bit we insert an error. The results are shown below.
The results we see are again what we would expect, the bit parity checks do not really have an effect on the eavesdroppers bit error rate. On the low iteration test we see that the bit error rate fluctuates - probably as we get rid of a good bit, and then keep a bad bit. As a result of these cancelling each other out, we see that the bit error rate stays constant.
Test Case 3
Test case 3 was again, another more realistic scenario than test case 2. Instead of having linear bit errors, say every 1 in 4, it is a programmed such that every 1/4, it generates a random number and this bit is then used as the error. It should create a more accurate representation of our scenario.
Again, we see similar results. This case is probably the most realistic as we see that the bit parity checks have some effect on the eavesdropper, however their bit error rate does not drop nearly as quickly as the sender/recipient, which is what we want to see.
Summary of Results
All of the tests show similar results - the bit error rate for the sender/recipient drops significantly while the bit error rate for the eavesdropper either stays constant, or drops very slowly in one of the test cases.
See also
- Timing-based key agreement
- Timing Based Encryption: Test Case 1
- Timing Based Encryption: Test Case 2
- Timing Based Encryption: Test Case 3
- Timing Based Encryption: Test Case 4
- Timing Based Encryption: Test Case 5
- Geometric Algebra
- CLUViz Geometric Algebra Animation Software
- Secure communications without key exchange (main page)
- Secure communications without key exchange? 2013 weekly progress
- Proposal Seminar 2013: Secure communications without key exchange?
- Final Seminar 2013: Secure communications without key exchange?
- Semester A Progress Report 2013 - Secure communications without key exchange?
- Semester B Final Report 2013 - Secure communications without key exchange? 2013
- YouTube Videos