Difference between revisions of "Final Report 2011"
(→Budget) |
(→Risk Management) |
||
| Line 383: | Line 383: | ||
{| border="1" cellspacing="0" style="text-align:center; margin: 1em auto 1em auto" | {| border="1" cellspacing="0" style="text-align:center; margin: 1em auto 1em auto" | ||
|- style="color:white; background:#191970; font-weight:bold" | |- style="color:white; background:#191970; font-weight:bold" | ||
| − | | width="220" | Risk || width="160" | Risk Estimation | + | | width="220" | Risk || width="160" | Risk Estimation || width="300" | Reduction Strategy |
|- style="background:#DCDCDC; font-weight:bold; text-align:left" | |- style="background:#DCDCDC; font-weight:bold; text-align:left" | ||
| colspan="4" | Physical Hazards | | colspan="4" | Physical Hazards | ||
|- | |- | ||
| − | | style="text-align:left" | External construction noise || style="background:#FFFF00" | Medium | + | | style="color:white; text-align:left; background:#4682B4" | External construction noise || style="background:#FFFF00" | Medium |
|- | |- | ||
| − | | style="text-align:left" | Falls within laboratory || style="background:#FFFF00" | Medium | + | | style="color:white; text-align:left; background:#4682B4" | Falls within laboratory || style="background:#FFFF00" | Medium |
|- | |- | ||
| − | | style="text-align:left" | Injuries due to electrical shock || style="background:#FFFF00" | Medium | + | | style="color:white; text-align:left; background:#4682B4" | Injuries due to electrical shock || style="background:#FFFF00" | Medium |
|- style="background:#DCDCDC; font-weight:bold; text-align:left" | |- style="background:#DCDCDC; font-weight:bold; text-align:left" | ||
| colspan="4" | Chemical Hazards | | colspan="4" | Chemical Hazards | ||
|- | |- | ||
| − | | style="text-align:left" | None || - | + | | style="color:white; text-align:left; background:#4682B4" | None || - || - |
|- style="background:#DCDCDC; font-weight:bold; text-align:left" | |- style="background:#DCDCDC; font-weight:bold; text-align:left" | ||
| colspan="4" | Biological Hazards | | colspan="4" | Biological Hazards | ||
|- | |- | ||
| − | | style="text-align:left" | None || - | + | | style="color:white; text-align:left; background:#4682B4" | None || - || - |
|- style="background:#DCDCDC; font-weight:bold; text-align:left" | |- style="background:#DCDCDC; font-weight:bold; text-align:left" | ||
| colspan="4" | Ergonomic Hazards | | colspan="4" | Ergonomic Hazards | ||
|- | |- | ||
| − | | style="text-align:left" | Work place layout || style="background:#00FF00" | Low | + | | style="color:white; text-align:left; background:#4682B4" | Work place layout || style="background:#00FF00" | Low |
|- style="background:#DCDCDC; font-weight:bold; text-align:left" | |- style="background:#DCDCDC; font-weight:bold; text-align:left" | ||
| colspan="4" | Radiation Hazards | | colspan="4" | Radiation Hazards | ||
|- | |- | ||
| − | | style="text-align:left" | None || - | + | | style="color:white; text-align:left; background:#4682B4" | None || - || - |
|- style="background:#DCDCDC; font-weight:bold; text-align:left" | |- style="background:#DCDCDC; font-weight:bold; text-align:left" | ||
| colspan="4" | Psychological Hazards | | colspan="4" | Psychological Hazards | ||
|- | |- | ||
| − | | style="text-align:left" | Work related stress || style="background:#FFFF00" | Medium | + | | style="color:white; text-align:left; background:#4682B4" | Work related stress || style="background:#FFFF00" | Medium |
|- | |- | ||
| − | | style="text-align:left" | Repetitive tasks || style="background:#FFFF00" | Medium | + | | style="color:white; text-align:left; background:#4682B4" | Repetitive tasks || style="background:#FFFF00" | Medium |
|- | |- | ||
|} | |} | ||
Revision as of 23:04, 22 October 2011
Contents
- 1 Under Construction
- 2 Introduction
- 3 Background Theory
- 4 Structural and Statistical Investigation
- 5 Cipher Investigation
- 6 CipherGUI
- 7 Pattern Matcher
- 8 Web Crawler
- 9 System Integration
- 10 Web Crawler Investigation
- 11 Future Development
- 12 Project Management
- 13 Project Outcomes
- 14 References
- 15 See also
- 16 References and useful resources
- 17 Back
Under Construction
Construction Notespace:
- Due to be finished 23/10/11 11:59pm
- Following structure is according to my report (mostly) so if the content you're uploading isn't consistent with the title just change the title.
- questions.. Project Outcomes before/after Management
Executive Summary
Introduction
History
The Case
The Code
Technological Progress
Previous Studies
Project Objectives
At the beginning of the project several broad objectives were established. These were:
- Comprehensive Cipher Analysis
- Create an ability to custom search the web
In the Comprehensive Cipher Analysis section the aim is to examine as many ciphers as possible and determine if each cipher can be ruled out as being used in encrypting the Somerton Man Code. This process intends to contribute to the ongoing cipher examination of the code.
The second objective aims at creating the ability to custom search and analyse the vast amounts of data available on the web that provides greater control than the average internet search engine. The reasoning behind this is the theory that with the amount of data available on the web, the true meaning of the code could already be written somewhere. Thus by exhaustively searching for distinct patterns evident in the code it may be possible to directly identify parts of the underlying message. This objective also includes the design aim of making the software flexible in that it could accept many different search patterns; providing applications beyond the scope of the Somerton Man investigation.
It should be noted that the project does not set the objectives of cracking the code nor solving the case. The code has not been solved in over 6 decades of attempts, so while the project does hope to shed some light on the meaning behind the code; the success of the project does not hinge on the code being cracked or the case being solved.
Extended Objectives
Group meetings throughout the course of the project identified areas on which the project objectives could be extended.
In the Cipher Analysis section a lot of software was being written for the process of investigating cipher links to the code. Rather than archive this software after each cipher was examined, an objective was set to utilise it by creating a centralised cipher analysis tool intuitively implementing numerous ciphers.
With the aim of designing web search software with numerous applications a need for a user-friendly interface was identified. This spawned the objective of creating an interactive user-friendly GUI from which to run the search mechanism from and present results through.
Finally, with these useful software applications, the goal was set to release them to the public by making them available on the project's wiki page.
Structure of Remainder of Report
Background Theory
Cipher Analysis
Web Crawler
Structural and Statistical Investigation
Concept
Given the fact the code was found in the back of the book of poems, Rubaiyat of Omar Khayyam, there remains suspicion that the code is somehow linked to the contents of the Rubaiyat. If this were the case, a cipher analysis may not even be necessary. This theory has been investigated by testing three hypotheses through statistically and structurally analysing the poems in the Rubaiyat.
Hypotheses
- The code is an initialism of a poem in the Rubaiyat
- Based on previous studies indicating an English initialism and the fact the code has four (un-crossed out) lines, with each poem being a quatrain (four line poem).
- The code is related to the initial letters of each word, line or poem
- Based on previous studies indicating an English initialism.
- The code is generally related to text in the Rubaiyat
- Based on the links between the Rubaiyat and the code.
Technical Challenges
The two main challenges in this analysis revolve around the source material.
- Code Ambiguities
- Sample Size
Code ambiguities refer to difficulties in determining which letters some of the handwritten symbols in the code represent; a challenge created by the untidy handwriting. Sample Size refers to the issues encountered due to the limited sample of 44 letters we have to analyse from the code.
Design of Tests
The approach to testing these hypotheses varied, although each used Java text parsing and statistic-gathering code. The first hypothesis was tested through statistically analysing the structure of the Rubaiyat poems and comparing to the Somerton Man code structure. The second and third hypotheses were tested through analysing letter frequencies in the poems using software and comparing these results to Somerton Man code letter frequencies. In the case of Hypothesis 2 frequency data was gathered on the first letter of each poem, the first letter of each line and the initial letter of each word. The third hypothesis similarly analysed letter frequencies of all letters in the Rubaiyat.
Results of Tests
Hypothesis 1: The code is an initialism of a poem. Statistics were gathered on the number of words in each line (first, second, third, fourth) of each poem. The statistics gathered include the mean number of words in each line, the standard deviation, the maximum number of words in a line and the minimum. The results categorized by line number in a Rubaiyat poem are shown in the table below, followed by the statistics from the Somerton Man’s code.
| Line | Mean | Std Dev | Max | Min |
| First | 8.00 | 1.15 | 10 | 5 |
| Second | 7.69 | 1.20 | 10 | 5 |
| Third | 7.88 | 1.06 | 10 | 5 |
| Fourth | 7.87 | 1.31 | 10 | 5 |
| Line | Number of Letters |
| First | 9 |
| Second | 11 |
| Third | 11 |
| Fourth | 13 |
The important result is the maximum number of words in the poem lines. Each line category has a maximum number of words of 10 across all of the 75 poems contained in the Rubaiyat. However, the code has 11, 11 and 13 letters in its second, third and fourth lines respectively, each over the maximum. These results allow Hypothesis 1 to be ruled out, giving the conclusion that the code is not an initialism of a Rubaiyat poem.
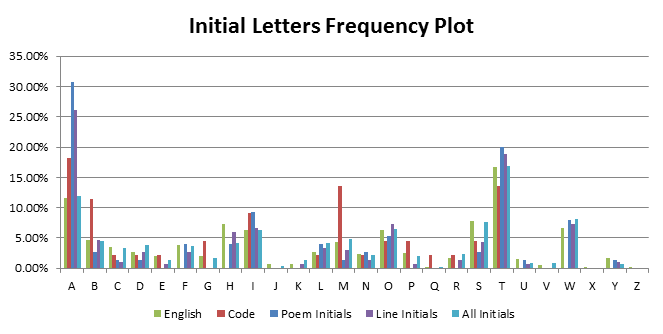
Hypothesis 2: The code is related to the initial letters of each word, line or poem. Letter frequency data was gathered on the first letter of each poem, of each line and of each word. This data is plotted against average English initial frequencies and the code letter distribution.
A link between poem initials or line initials and the code can be trivially ruled out. There is a ‘G’ in the code but no line or poem starts with a ‘G’ in the entire Rubaiyat. A link between all initial letters in the Rubaiyat and the code is more difficult to rule out. There is a generally good correlation between English initials and initials in the Rubaiyat (graphed in light blue) as might be expected, but there are significant discrepancies when compared to the code, such as the code clearly having a greater proportion of A’s, B’s and M’s. While a link cannot be ruled out due to the small sample size of the code (44 letters), for the purposes of this project a link has been ruled unlikely.
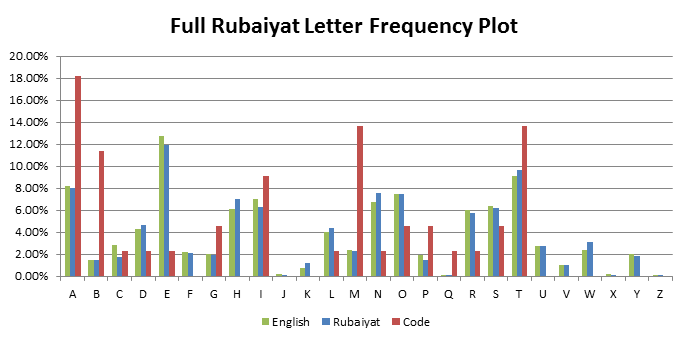
Hypothesis 3: The code is generally related to the text in the Rubaiyat. This hypothesis was tested by adapting the Java text parser code to generate letter frequency plots for the all letters in the Rubaiyat poems. The results are displayed in the graph below.
While there is very good correlation between the Rubaiyat poems and English text, the letter frequency of the code is substantially different, with significantly larger proportions of M’s, A’s and B’s. Again the sample size of 44 letters for the code restricts our ability to make a conclusion, but for our purposes there is enough evidence to discount a link.
Conclusions
The rejection of these three hypotheses indicates there is no direct (unencrypted) link between the code and the Rubaiyat, disregarding the weaknesses surrounding the assumptions required with ambiguous letters and the small sample size. This result, combined with the 2009 and 2010 results indicating the code was not random[1][2], led to the conclusion that the project did require a comprehensive cipher analysis. It should be noted that this conclusion doesn’t rule out all links between the code and the Rubaiyat; just unencrypted links.
Cipher Investigation
Concept
Previous Work
Technical Challenges
Methodology
Results
| Cipher | Test techniques | Status | Student |
| ADFGVX | Structural analysis | Disproven | Steven |
| Affine | Direct decryption | Disproven | Patrick |
| Alphabet reversal | Direct decryption | Disproven | Patick |
| Auto-key | Direct decryption | Disproven | Steven |
| Baconian | Structural analysis | Disproven | Patick |
| Beaufort | Frequency analysis | Unlikely | Steven |
| Bifid | Frequency analysis | Disproven | Steven |
| Book | Structural analysis | Disproven | Patrick |
| Dvorak encoding | Direct decryption | Disproven | Patrick |
| Flat-frequency | Statistical analysis | Disproven | Patrick |
| Four square | Structural analysis | Unlikely | Patrick |
| Gronsfeld | Structural analysis | Disproven | Steven |
| Hill | Frequency analysis | Disproven | Steven |
| Homophonic substitution | Structural analysis, Statistical analysis | Disproven | Patrick |
| Keyword | Frequency analysis | Possible | Patrick |
| Nihilist | Structural analysis | Disproven | Steven |
| Null | Structural analysis | Unlikely | Patrick |
| Number based | Structural analysis | Disproven | Patrick |
| One time pad | Statistical analysis | Unlikely | Patrick |
| Pigpen | Direct decryption | Disproven | Patrick |
| Playfair | Structural analysis | Disproven | Patrick |
| Playfair (Double) | Frequency analysis | Unlikely | Steven |
| Porta | Frequency analysis | Unlikely | Steven |
| Rail fence | Direct decryption | Disproven | Patrick |
| Shift | Direct decryption | Disproven | Steven |
| Templar | Direct decryption | Disproven | Steven |
| Trifid | Frequency analysis | Unlikely | Steven |
| Trithemius | Direct decryption | Disproven | Steven |
| Two square | Structural analysis | Unlikely | Patrick |
| VIC | Structural analysis | Disproven | Steven |
| Vigenere | Frequency analysis | Unlikely | Steven |
CipherGUI
Concept
Technical Challenges
Design
Implementation
Testing
Pattern Matcher
Concept
Previous Work
Technical Challenges
Design
Implementation
Testing
Web Crawler
Concept
Previous Work
Technical Challenges
Design
Implementation
Testing
System Integration
Concept
Previous Work
Technical Challenges
Design
Implementation
Testing
Web Crawler Investigation
Concept
Technical Challenges
Design
Results
Future Development
Cipher Analysis
Web Crawler
Project Management
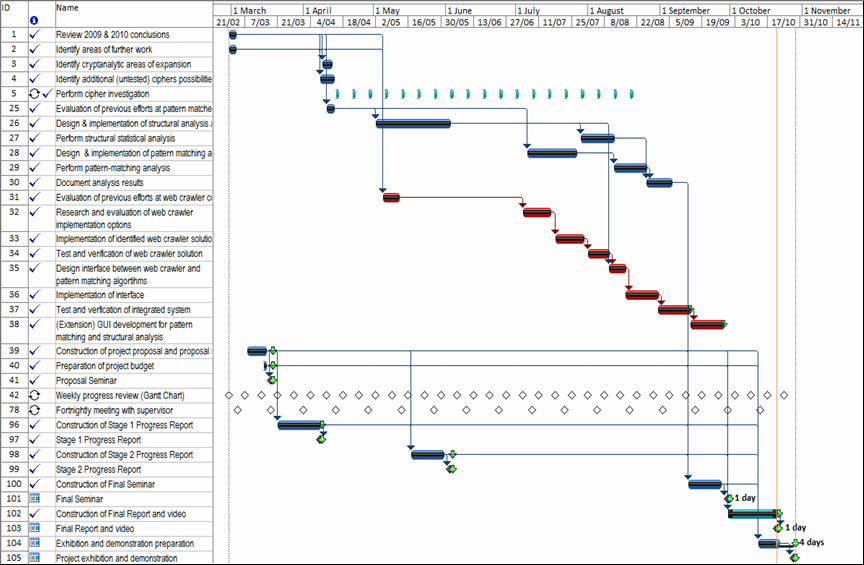
Timeline
| Milestone | Description | Due | Met | Status |
| Cipher and Structural Investigations | ||||
| Analysis of Rubaiyat | Report on Rubaiyat links complete | 08/08/11 | 01/06/11 | Completed ahead of schedule |
| Cipher Identification | Cipher List compiled | 10/04/11 | 17/03/11 | Completed ahead of schedule |
| Cipher Investigation | Cipher List fully investigated | 16/08/11 | 30/08/11 | Completed behind schedule |
| (Extension) CipherGUI | Passes final tests | 01/10/11 | 26/10/11 | Completed ahead of schedule |
| Web Crawler Development | ||||
| Pattern Matcher module | PM successfully detects patterns and returns results | 08/08/11 | 15/07/11 | Completed ahead of schedule |
| Web Crawler module | WC self-navigates the web | 08/08/11 | 08/08/11 | Completed on schedule |
| System Integration | Software retrieves web pages and matches patterns | 17/09/11 | 17/09/11 | Completed on schedule |
| (Extension) GUI complete | Able to run searches and view results from GUI | 25/09/11 | 27/09/11 | Completed behind schedule |
| Project Management | ||||
| Proposal Seminar | Proposal Seminar presented | 18/03/11 | 18/03/11 | Completed on schedule |
| Stage 1 Progress Report | S1PR submitted | 01/04/11 | 01/04/11 | Completed on schedule |
| Stage 2 Progress Report | S2PR submitted | 03/06/11 | 03/06/11 | Completed on schedule |
| Final Presentation | Presentation presented with demonstration | 30/09/11 | 30/09/11 | Completed on schedule |
| Final Report | Final Report handed over | 21/10/11 | 21/10/11 | Completed on schedule |
| Project Exhibition and Poster | Poster complete and Exhibition given | 28/10/11 | 28/10/11 | Progress on schedule |
| Project Video | Video complete and uploaded to YouTube | 28/10/11 | 28/10/11 | Progress on schedule |
| Handover | Products and results handed over to EEE School | 28/10/11 | 28/10/11 | Progress on schedule |
Role Allocation
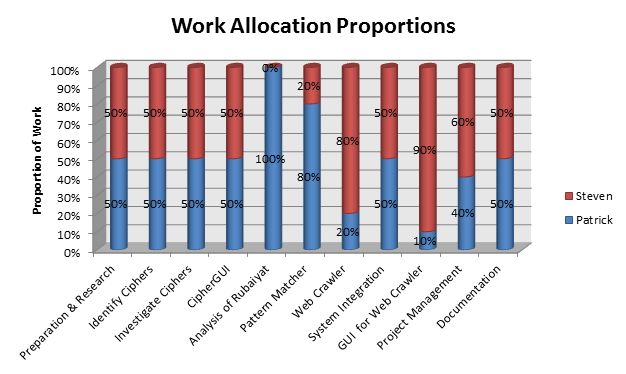
During the planning phase of the project, a workload allocation plan was specified, recognising that while some areas could be worked on equally, there were distinct advantages in individual team members focusing on specialty areas. A graphical illustration of allocations is shown in the figure below, with reasoning provided underneath.
The review and research of previous work was split equally since each project member needed to have a good understanding of the entire project and its status. The workload in the Cipher Analysis section (including the CipherGUI) was also equally shared. This was due to the compartmentalised nature of the cipher investigation; individual ciphers were all separate investigations so there was no major advantage in specialising.
Recognising the complexity and distinct segments of the web crawler application, the development of the pattern matching and web crawler modules were assigned to Patrick and Steven respectively. The reasoning behind this was Patrick’s previous experience in active file-searching, whilst Steven’s overall greater exposure to University Computer Science courses was expected to give an advantage in the challenges encountered in developing the web crawling module. System integration between these modules was split equally. Steven’s GUI design experience was the motive behind being assigned the development of the Web Crawler System GUI, while the pattern matching experience made it logical for Patrick to take responsibility for the structural and statistical analysis of the Rubaiyat which involved writing statistic gathering software. Project management and documentation were both shared.
Review and Audit Process
The process of reviewing and auditing progress and revising group member roles was well managed throughout the lifecycle of the project. The strategy used focused on several key areas:
- Regular (internal) meetings and Gantt chart
- Project wiki page
- svn Repository
- Extensive email Communication
A minimum of one informal meeting per week was held between project members to discuss progress and ensure both Patrick and Steven were satisfied with the current status. These meetings provided a platform to discuss individual challenges encountered and brainstorm solutions to these problems. They also enabled members to query each other’s work to ensure it was at a satisfactory level of quality.
The project wiki page played two main roles. Firstly, the Weekly Progress page was updated each week by both team members. This provided both a self-check mechanism to ensure goals were being achieved and an additional update for the other group member as to their counterpart’s progress. Secondly, shared database areas, such as the Cipher Cross-off List, enabled group members to review each other’s work ensuring it was comprehensive and of high quality.
The svn repository requested from the School of Electrical and Electronic Engineering proved extremely valuable as both an auditing function and a work integration tool. The repository was used extensively throughout the project for both the CipherGUI and the Web Crawler system. The top level of the repository is shown in the image below.
Finally, a high level of communication played a key role in organising and collaborating project work. Communication was both in person and through the University email system including the Gmail chat functionality. Without this high level of communication, it is unlikely the project would have been as successful as it was, nor achieved nearly as much as it did.
It may be noted that in the Work Allocation graph displayed in the previous section, tasks allocated to one project member were not completed 100% by that member. While partially due to the team self-auditing approach resulting in both members working on sections, there was also an aspect of role re-assignment responsible. Role re-assignment was primarily due to differing workloads combining with schedule requirements. Role re-assignment was organised both through email communications channels and at the regular internal group meetings.
Budget
| Item | Projected cost | Cost |
| Bay Discovery Centre Exhibition | $4.00 | $4.00 |
| Additional printing (Project Exhibition) | $60.00 | $30.00 |
| Total used: | $64.00 | $34.00 |
| Total provided: | $500.00 | $500.00 |
Risk Management
| Risk | Risk Estimation | Reduction Strategy |
| Availability of personnel | High | Regular meetings with flexible schedule |
| Insufficient financial resources | Medium | Open source software and project budget |
| Software development tool access | High | Suitable personal work environment on laptop for each team member |
| Unable to maintain software development schedule | Medium | Progress management strategy |
| The Somerton Man case is solved | Low | No risk reduction strategy |
| Risk | Risk Estimation | Reduction Strategy | |
| Physical Hazards | |||
| External construction noise | Medium | ||
| Falls within laboratory | Medium | ||
| Injuries due to electrical shock | Medium | ||
| Chemical Hazards | |||
| None | - | - | |
| Biological Hazards | |||
| None | - | - | |
| Ergonomic Hazards | |||
| Work place layout | Low | ||
| Radiation Hazards | |||
| None | - | - | |
| Psychological Hazards | |||
| Work related stress | Medium | ||
| Repetitive tasks | Medium | ||
Project Outcomes
Significance and Innovations
Strengths and Weaknesses
Conclusion
References
- ↑ https://www.eleceng.adelaide.edu.au/personal/dabbott/wiki/index.php/Final_report_2009:_Who_killed_the_Somerton_man%3F
- ↑ https://www.eleceng.adelaide.edu.au/personal/dabbott/wiki/index.php/Final_Report_2010
See also
- Glossary
- Cipher Cross-off List
- Stage 1 Design Document 2011
- Stage 2 Progress Report 2011
- Final Seminar Recording 2011 Part 1
- Final Seminar Recording 2011 Part 2
- Final Seminar Recording 2011 Part 3
References and useful resources
- Final Report 2010
- Final report 2009: Who killed the Somerton man?
- Timeline of the Taman Shud Case
- The taman shud case
- Edward Fitzgerald's translation of رباعیات عمر خیام by عمر خیام
- Adelaide Uni Library e-book collection
- Project Gutenburg e-books
- Foreign language e-books
- UN Declaration of Human Rights - different languages
- Statistical debunking of the 'Bible code'
- One time pads
- Analysis of criminal codes and ciphers
- Code breaking in law enforcement: A 400-year history
- Evolutionary algorithm for decryption of monoalphabetic homophonic substitution ciphers encoded as constraint satisfaction problems