Final Report 2011
Under Construction
Construction Notespace:
- Due to be finished 23/10/11 11:59pm
- Following structure is according to my report (mostly) so if the content you're uploading isn't consistent with the title just change the title.
- questions.. Project Outcomes before/after Management
Executive Summary
Introduction
History
The Case
The Code

Technological Progress
Previous Studies
Project Objectives
Extended Objectives
Structure of Remainder of Report
Background Theory
Cipher Analysis
Web Crawler
Structural and Statistical Investigation
Concept
Given the fact the code was found in the back of the book of poems, Rubaiyat of Omar Khayyam, there remains suspicion that the code is somehow linked to the contents of the Rubaiyat. If this were the case, a cipher analysis may not even be necessary. This theory has been investigated by testing three hypotheses through statistically and structurally analysing the poems in the Rubaiyat.
Hypotheses
Technical Challenges
Design of Tests
Results of Tests
| Line | Mean | Std Dev | Max | Min |
| First | 8.00 | 1.15 | 10 | 5 |
| Second | 7.69 | 1.20 | 10 | 5 |
| Third | 7.88 | 1.06 | 10 | 5 |
| Fourth | 7.87 | 1.31 | 10 | 5 |
| Line | Number of Letters |
| First | 9 |
| Second | 11 |
| Third | 11 |
| Fourth | 13 |
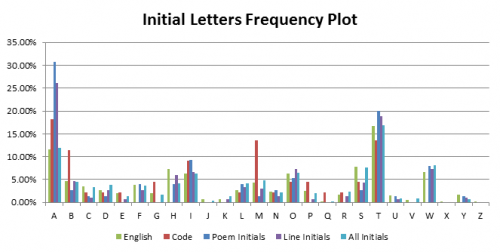
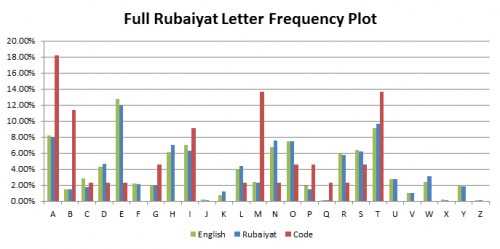
Cipher Investigation
Concept
Previous Work
Technical Challenges
Methodology
Results
CipherGUI
Concept
Technical Challenges
Design
Implementation
Testing
Pattern Matcher
Concept
Previous Work
Technical Challenges
Design
Implementation
Testing
Web Crawler
Concept
Previous Work
Technical Challenges
Design
Implementation
Testing
System Integration
Concept
Previous Work
Technical Challenges
Design
Implementation
Testing
Web Crawler Investigation
Concept
Technical Challenges
Design
Results
Future Development
Cipher Analysis
Web Crawler
Project Management
Timeline
Role Allocation
Review Process
Budget
Risk Management
Project Outcomes
Significance and Innovations
Strengths and Weaknesses
Conclusion
References
See also
- Glossary
- Cipher Cross-off List
- Stage 1 Design Document 2011
- Stage 2 Progress Report 2011
- Final Seminar Recording 2011 Part 1
- Final Seminar Recording 2011 Part 2
- Final Seminar Recording 2011 Part 3
References and useful resources
- Final Report 2010
- Final report 2009: Who killed the Somerton man?
- Timeline of the Taman Shud Case
- The taman shud case
- Edward Fitzgerald's translation of رباعیات عمر خیام by عمر خیام
- Adelaide Uni Library e-book collection
- Project Gutenburg e-books
- Foreign language e-books
- UN Declaration of Human Rights - different languages
- Statistical debunking of the 'Bible code'
- One time pads
- Analysis of criminal codes and ciphers
- Code breaking in law enforcement: A 400-year history
- Evolutionary algorithm for decryption of monoalphabetic homophonic substitution ciphers encoded as constraint satisfaction problems